2.7 million medical calls breached in Sweden, and it's pure comedy
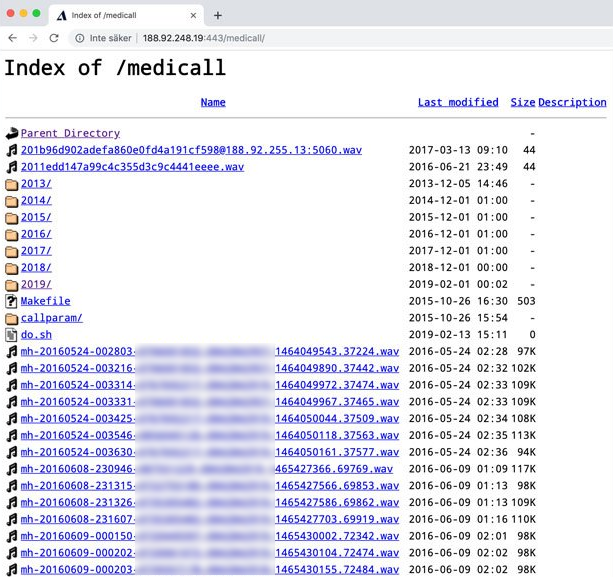
On Monday, news outlet Computer Sweden broke the news that millions of calls to a national Swedish health care adviser were openly available on the internet. Here is a summary in English. In short, they were recording calls for years, put them on a NAS and connected it to the internet, unencrypted, with no password protection. Caller phone numbers were displayed in the file names.
Why is this funny? It isn’t. It is extremely serious, and I sincerely hope that we fill see massive fines, people lose their jobs, and perhaps some more severe criminal charges brought against those whose negligence caused this1.
But it is also funny. Because the incompetence reads like a Monty Python sketch, or like the “front fell off” video.
I made a Facebook post in Swedish that got some attention, so I figured I would make it available to you English speakers out there as well. I know most of the conversation on this is going on in Swedish, so I want to make sure you get in on the tragedy/comedy. At the bottom of the post, I’m collecting my favorite quotes. Read ‘em and weep.
Here’s the original post. English translation below. I have truly made my best effort to convey the silliness. Some quotes may sound badly translated, but I assure, they sound just as inane in Swedish. I’ll drop sic markers in liberally to avoid any confusion.
Original Facebook post
I know I have many friends and acquaintances who are not familiar with IT jargon, which is naturally being used a lot by the culprits in this matter as they defend themselves. I’m sure many of you feel that this was a serious accident, something unpredictable, an unfortunate but inevitable side-effect of digitalization.
This is not the case.
Every coder I have read, heard and talked to are thrown between bursting into laughter and bursting into tears. Every interview about this sounds like a Monty Python sketch.
It is painfully obvious that no one involved in this knows the first thing about computer security, and barely anything about IT. Digitalization did not cause the 11772 fiasco. Absurd levels of incompetence were the cause. Truly absurd.
So this seems like a problem with procurement, and consultants promising much while knowing little. The whole thing seems like a systems-level Dunning–Kruger effect: people have so little knowledge that they don’t realize how little they know, so they assume their solutions are alright. They also don’t grasp how little everyone else involved knows, and suddenly the blind are leading the blind. It takes very small amounts of competence to realize that data of this sensitive nature requires extra care, that you need to find out what you don’t know, that you need to ask for help. Not just connect the damn thing and cross your fingers.
In this status, I will collect my favorite quotes from involved parties in this debacle as I come across them because this is comedy gold. The stupidity is mind-numbing.
Tommy Ekström, CEO of Voice Integrate Nordic AB, the ground-zero of the breach
- “It’s an internal hard drive, so to speak, that isn’t password protected since it’s only accessible from the computer it’s connected to.3”
- “A regular person can’t do it, but those who are knowledgeable about these things could perform some sort of special command move [sic] and sneak in through the back.4”
- “It’s comparable to a personal home hard drive. You don’t perform surveillance for breaches, because it can’t be accessed.”
- “For some reason, it has gotten its own little[sic] cord to the Internet. It wouldn’t have hurt if no one knew this server had this problem[sic], but Computer Sweden found out.”
- “You can’t protect yourself 100 percent from these things, but we have to look over our routines, and we’re doing that now. If we upgrade this kind of servers we have to check if they are connected to the Internet. Like a checklist when you land an airplane. These kinds of incidents are caused by having many people in rotation, not any intentional mischief.5”
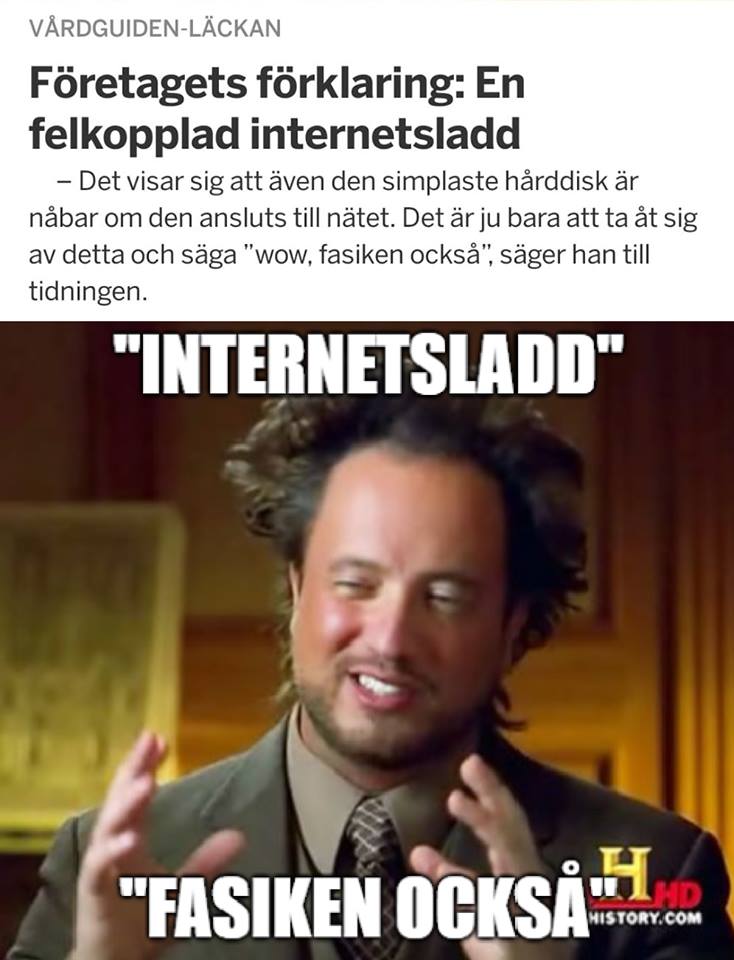
- “But it turns out even the simplest hard drive is accessible if it’s connected to the Internet.”
- Tommy Ekström said they have now pulled the Internet cord and closed the server off from the Internet6.
- According to Ekström, 55 files have been downloaded from the drive, “many of them duplicates”.
- Tommy Ekström says that Voice Integrate Nordic is initially investigating themselves, but external auditors may become involved later. “We have people who are extremely competent in these matters.7”
- “They don’t have to worry, their information is not released [sic]. The files that have been downloaded is not a large quantity, and we know who they are.8”
- “At the same time, if you have advanced technology [sic] you can’t protect yourself against everything.9”
- “These days it’s not as easy as just having a server with everything on it, it’s a bunch of hassle with lots of people involved, lots of parts outside our own company.”
- “We use Applion10 because their certificate handling is so good.11”
- “Are you saying there is no username and password for the server?”
- “That someone probably, when updating at some point, seen that there was a free networking cable slot, and I guess they thought, some technician: ‘Aha, there should probably be a cable here, but it fell out [sic]’, and then they have connected a networking cable, so that it’s become connected to the Internet. That is just, like, how you do these things.12”
 Translation:
Translation:
“It turns out even the simplest hard drive is accessible if it is connected to the Internet. All you can do is learn from this and say ‘wow, gosh darn it’, he said to the paper.”
“Internet cable”
“Gosh darn it”
Davide Nyblom, CEO of MediCall, confronted with the news
- We have checked with our IT department, and what you are saying is completely impossible.”
Voice Integrate Nordic’s website 2019-02-20
- “The server is no longer accessible because we have ‘PULLED THE CORD’ [sic] and we are continuing to analyze what happened.”
- “We have taken some ‘flak’ for this event, but we are trying to stay focused on minimizing damage and correcting the error.13”

MediCall’s website
- “February 18 a breach was detected at MediCall’s and MedHelp’s subcontractor Voice Integrate Nordic AB.14”
- “The server is located in Sweden and no patient data or personal information is stored outside Swedish borders.15”
Björn Arkinger, business area manager at MedHelp
- When asked why they don’t hire penetration testers: “Well, that’s a good question. I mean, one should be aware that these kinds of solutions are handled by very complex systems. It’s hard.16”
- “I would say that the average person is knowledgeable enough to reach them. You had to perform a port scan on the server, and it would take a certain amount of effort.17”
Other humor
These very 90s websites:
Sources
DN, ComputerSweden, Aftonbladet, P1
- https://www.aftonbladet.se/nyheter/a/3jALML/ansvariga-om-vardsamtalen-far-inte-handa
- https://sverigesradio.se/sida/avsnitt/1239014?programid=1650&fbclid=IwAR2nIR8Y-9KiRcc6YvYEa_CkbqFkLwcsRics4GhtqekApAFSndq6DsfG_4g (2:15:48)
- https://www.dn.se/ekonomi/ansvarig-for-vardguiden-haveriet-manskliga-faktorn/?fbclid=IwAR14_QKkvBsU95SHtBb1FggBQCPztWqQZ_4iS5uoqdaD36qdkbbIbp5ICF4
- https://computersweden.idg.se/2.2683/1.714787/inspelade-samtal-1177-vardguiden-oskyddade-internet
Disclaimer
I’m not a security expert. I’m just a computer scientist, I work a lot with computers, and I hang around people who are much better at networking and security than I am. So I don’t know what is best practice, and I’m sure there are things that sound silly to me that are actually reasonable, as well as quotes I find completely normal that are actually madness. Please let me know.
-
This sentence got me some valid criticism about not addressing things on the system level, so I elaborated a bit on it. You can follow the discussion here. ↩
-
1177 is the number you call for this healthcare advisory service. The service is therefore known as 1177, and this whole affair goes under that name, for now. ↩
-
Please, please, if you are storing sensitive data, also password protect your hard drives! ↩
-
All of the records were available at 188.92.248.19:443/medicall, which anyone could point their browser to. Despite being on the 443 port, it was serving everything through regular HTTP, no encryption or credentials required. ↩
-
It’s funny because this is like a pilot shutting off one engine and trying to land backward, then blaming the wreck on a lack of routines. ↩
-
Very funny, because you have already shown an extreme lack of competence, and the company has only 3 employees. ↩
-
They have previously stated that they know the IP addresses of clients that have accessed the server and that they are from “regular internet providers”. If they think that means they can track the clients, they are in for a big surprise. ↩
-
But if you have simple, off-the-shelf technology, like yours, could you maybe put up a minimum of a security perimeter? ↩
-
Which is their sister company. ↩
-
Click that link. It’s a great website. ↩
-
PSA: That is not how you do these things. Please stop operating in this manner. It sounds like a dude who knows how to plug in his own wifi at home, and maybe configure his own printer – just put cables in the empty slots with the right colors – and assumed that is an adequate modus operandi for a government contractor handling extremely sensitive patient data. ↩
-
You are not the victim here. Don’t you dare whine about the mess you caused. ↩
-
If you get a call from a journalist looking at your sensitive data and responding by asking if it wasn’t password protected, I wouldn’t call that ‘detecting a breach’. I wish the involved companies would drop their bullshit we-know-what-we’re-doing lingo, which they are also often using incorrectly. ↩
-
That is absolutely irrelevant if it is accessible by a goddamn browser. Note also that MediCall is based in Thailand, so if they access this data (which, remember, was served unencrypted), that means the data is crossing borders. ↩
-
Recording VoIP calls and putting them on a NAS via HTTP is not a Very Complex System™. Don’t make it sound like you are a big, knowledgeable IT company, and that this is the result of the complexity of modern IT. ↩
-
Finding it was a matter of knowing the IP, and to think to look there. It’s like hiding your house key under your rug – it’s fine as long as no one makes the minimal effort of breaking in. And saying it takes a port scan is ridiculous: it was on port 443, which would be in the top 3 you would try first. ↩